Easy, efficient and secure backup for any workload
Overcoming the growing complexity of IT infrastructures and sophisticated cyberattacks requires a comprehensive backup solution to keep every bit of data safe.
Acronis Cyber Protect integrates backup with advanced anti-ransomware technologies to keep your data safe from any threat.
- 20+ platforms protectedSafeguard data across physical, virtual, cloud and mobile environments.
- Quick, reliable recoveryGet fast and reliable recovery of your apps, systems and data on any device, from any incident.
- Secure ransomware protectionDefend your data with built-in MI-based ransomware protection and blockchain notarization.
File and disk-image backup
Backup individual files or safeguard your entire business by backing up the entire system as a single file, ensuring a bare metal restore capability. In the event of data disaster, you can easily restore all information to new hardware.
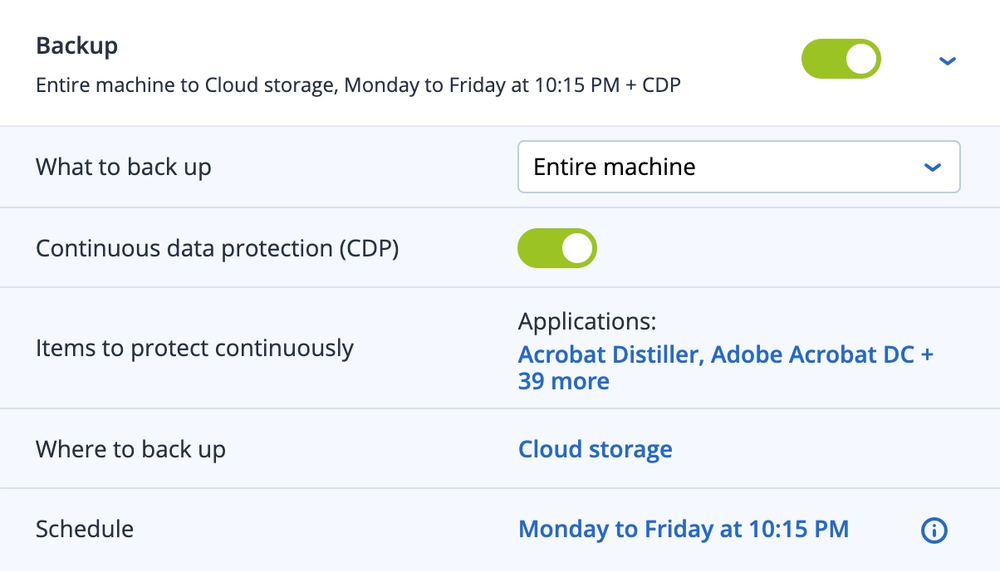
Continuous data protection
Ensure users don’t lose their in-progress work by defining a list of critical apps that are frequently used. Acronis’ agent monitors every change made in the listed applications—no matter where the user saves the file – and continuously backs it up. If the system needs to be reimaged, you can restore the data from a backup and apply the latest changes, so no data is lost.
- Flexible storageBalance the value of data, infrastructure and any regulatory requirements with flexible storage options. Grow with ease using the storage that fits your needs: NAS, SAN, tapes, disks, Acronis Cloud or any private or public cloud, such as Azure, AWS or Google.
- Any-to-any migrationAcronis stores data in a unified backup format so that you can easily recover to any platform, regardless of the source system. Reduce risk and IT overload by migrating between different hypervisors and to/from physical machines (P2V, V2V, V2P and P2P) or the cloud (P2C, V2C, C2C, C2V and C2P).
- Acronis Universal RestoreMinimize expensive downtime by restoring Windows and Linux systems to dissimilar hardware, including bare-metal physical, virtual or cloud environments. By overcoming compatibility issues, Acronis Universal Restore technology ensures quick and easy system migration with a few clicks.
- Acronis Instant RestoreReduce recovery times with best-in-industry RTOs by immediately starting your backup as a Windows or Linux virtual machine directly from storage. Have your VM up and running in mere seconds, while Acronis Instant Restore technology invisibly moves your data to the host in the background.
- Variable block-size deduplicationProtect more systems while reducing the impact on disk-storage and network capacity by capturing only the blocks with data that has changed since the previous backup. Acronis Cyber Backup deduplication minimizes storage space by detecting data repetition and storing the identical data only once.
- Data protection across 20+ platformsEvery system—physical, virtual or cloud—and all workloads are consolidated to safeguard data across all platforms. Any new application is integrated seamlessly into your existing environment, delivering continuous and comprehensive data protection.
- Drive health monitoringAvoid unpredictable data loss and proactively improve uptime by monitoring drive health. By using machine learning on S.M.A.R.T. reports, and various operating system parameters, Acronis Cyber Protect can alert you about a disk issue before it happens. This enables you to take the precautionary measures needed to protect your data.
- UNIQUEAnti-malware scanning of backupsPrevent restoring infected files from backups with built-in malware scanning. By scanning full disk backups at a centralized location, Acronis Cyber Protect can help find malware – ensuring users restore a clean, malware-free backup.
- UNIQUESafe RecoveryAn OS image or application in a backup that is infected with malware can cause continuous reinfection if it is used for recovery without removing the malware. Removing the detected malware and applying the latest anti-malware definitions during the recovery allows users to restore the OS image safely, reducing the chance of reinfection.
- UNIQUEData Protection MapEnsure that critical data is protected for compliance reporting with a data protection map. Get detailed information about stored data and use the automatic data classification to track the protection status of important files. You will be alerted if files are backed up or not, helping you to further protect your data.
- UNIQUEApp allowlisting based on backups contentsTraditional, global allowlisting does not handle custom applications well. Acronis Cyber Protect scans backups with anti-malware technologies (MI, behavioral heuristics, etc.) to allowlist organizationally unique apps and avoid future false positives.
- UNIQUEForensic data collectionMaintaining compliance and running internal investigations can be an expensive process. With the Forensic Mode built into Acronis Cyber Protect, you can simplify future analysis by collecting digital evidence – like memory dumps and process information – from disk-level backups.
- Tape MultiplexingMaximize the effective use of tape drives during backup and recovery by allowing multiple clients to back up to a single tape drive simultaneously. Use this method when a tape drive is faster than the backup source, as it allows the tape drive to keep spinning, avoiding writing interruptions.
- Tape MultistreamingUtilize all available tape devices on your system by allowing the backup of a single client to run simultaneously to multiple tape drives. Use this method when you have multiple destination devices and would like a single backup job to utilize them all simultaneously at the time of backup.





